Log in to server
cd to ..htdocs/qubecom/students/
to switch off
cp print_credit.php-servicedisabled print_credit.php
to switch on
cp print_credit.php-serviceok print_credit.php
Web related articles
Log in to server
cd to ..htdocs/qubecom/students/
to switch off
cp print_credit.php-servicedisabled print_credit.php
to switch on
cp print_credit.php-serviceok print_credit.php
Checking the Apache server-status page I noticed multiple lines like the following:
| 29-39 | – | 0/0/3162 | . | 32.26 | 8949 | 0 | 0.0 | 0.00 | 186.48 | 123.111.123.111 | mywebsite.co.uk | OPTIONS * HTTP/1.0 |
| 30-39 | – | 0/0/10 | . | 0.00 | 24324 | 0 | 0.0 | 0.00 | 0.04 | 123.111.123.111 | mywebsite.co.uk | OPTIONS * HTTP/1.0 |
The access_log for that website also showed:
123.111.123.111 – – [18/Nov/2009:09:28:44 +0000] “OPTIONS * HTTP/1.0” 200 – “-” “Apache/2.2.3 (Red Hat) (internal dummy connection)” 2468
123.111.123.111 – – [18/Nov/2009:09:35:37 +0000] “OPTIONS * HTTP/1.0” 200 – “-” “Apache/2.2.3 (Red Hat) (internal dummy connection)” 1924
Apparently these are Apache calling itself to keep child processes alive:
When the Apache HTTP Server manages its child processes, it needs a way
to wake up processes that are listening for new connections. To do
this, it sends a simple HTTP request back to itself.
Not all crawlers obey all of these rules but as a reference point. The crawl delay is the number of seconds between requests and the newer request-rate is set here to not more than 1 every 5 seconds. The crawlers are also asked to visit during the night.
User-agent: *
Disallow: /media/
Crawl-delay: 10
Request-rate: 1/5
Visit-time: 2100-0545
I was testing authentication against Active Directory (LDAP) using Apache 2. The following worked for me in a .htaccess file but only after adding:
LDAPVerifyServerCert Off
in the main httpd.conf file. I presume this is related to the server name in the SSL certificate on the Active Directory server.
AuthBasicProvider ldap
AuthzLDAPAuthoritative Off
AuthLDAPURL ldaps://adserver.prefix.tld.co.uk:636/DC=prefix,DC=tld,DC=co,DC=uk?sAMAccountName?sub?(objectClass=user)
AuthLDAPBindDN “CN=someuser,OU=some ou,OU=another unit,OU=department,OU=directorate,OU=Administration,OU=another big unit,DC=prefix,DC=tld,DC=co,DC=uk”
AuthLDAPBindPassword secret
AuthType Basic
AuthName “Protected”
require valid-user
Normal users should then be prompted for a username and password to access the directory and if correct credentials are supplied should be given access to the content.
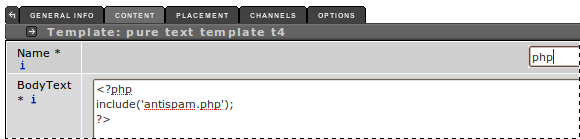
The CMC team have implemented an anti-spam measure to reduce comment form spam. The following instructions explain how to use this from within the Terminal 4 content management system. The result is that before your form is displayed the users IP address is checked against a list of known spammers – so there may be a 1 second delay before the form is displayed.

To redirect requests from http to https, create the .htaccess file with the following:
RewriteEngine On
RewriteCond %{SERVER_PORT} !443
RewriteRule (.*) https://website.com/path [R]